需要抓取Kerberos协议交互认证的数据包,想了想最简单的方式应该就是在Web服务的基础上增加Kerberos认证了。
环境说明 整个测试环境的搭建采用三台Ubuntu 18.04虚拟机,均修改了hosts文件:
1 2 3 192.168.1.118 tmp 192.168.1.134 sakura 192.168.1.113 dev
其中:192.168.1.118为Web服务器,采用Apache2192.168.1.134为KDC Server192.168.1.113为客户端
配置KDC Server 1 $ apt install krb5-admin-server krb5-kdc
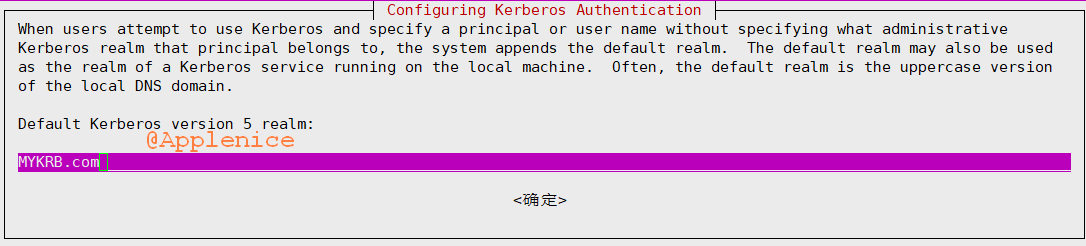
提供Realm:
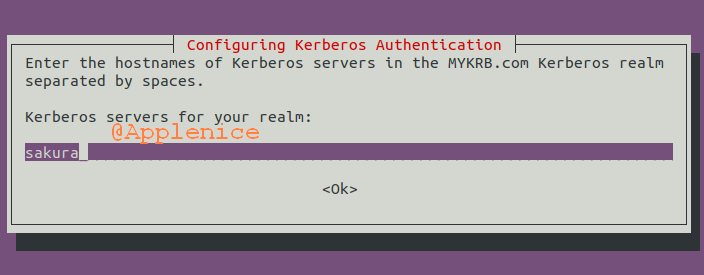
提供Kerberos Server FQDN,输入KDC Server所在机器的hostname
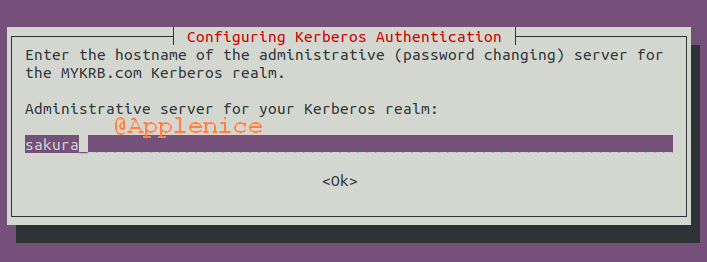
配置krb5 Admin Server
中间配置出问题需要卸载重来的,可以执行:
1 $ apt purge -y krb5-kdc krb5-admin-server krb5-config krb5-locales krb5-user krb5.conf
上面配置完毕后,执行krb5_newrealm来初始化Kerberos Realm:
执行完毕后,确认/etc/krb5kdc/kadm5.acl和/etc/krb5.conf的配置:
1 2 3 4 5 6 7 $ cat /etc/krb5kdc/kadm5.acl # This file Is the access control list for krb5 administration. # When this file is edited run service krb5-admin-server restart to activate # One common way to set up Kerberos administration is to allow any principal # ending in /admin is given full administrative rights. # To enable this, uncomment the following line: */admin *
1 2 3 4 5 6 $ cat /etc/krb5.conf [realms] MYKRB.com = { kdc = sakura admin_sercer = sakura }
启动服务:
1 2 $ systemctl start krb5-kdc $ systemctl start krb5-admin-server
配置Web服务 Apache 安装Apache2
1 2 $ apt install apache2 $ systemctl status apache2
创建测试文件:
1 $ echo 'Hello Kerberos' > /var/www/html/krb5_hello.txt
重启服务器后,通过curl进行访问测试:
1 2 3 4 5 6 7 8 9 10 11 $ curl -i http://tmp/krb5_hello.txt HTTP/1.1 200 OK Date: Sat, 24 Oct 2020 16:51:47 GMT Server: Apache/2.4.29 (Ubuntu) Last-Modified: Sat, 24 Oct 2020 15:32:55 GMT ETag: "f-5b26c6942a142" Accept-Ranges: bytes Content-Length: 15 Content-Type: text/plain; charset=UTF-8 Hello Kerberos
GSSAPI 使用GSSAPI在编写应用程序时,可以应用通用的安全机制。开发者不必针对任何特定的平台、安全机制、保护类型或传输协议来定制安全实现,可忽略保护网络数据方面的细节。许多底层机制和技术(如Kerberos v5或公钥技术)都支持GSSAPI框架。
这里我们通过mod_auth_gssapi给Apache2增加验证功能。
1 $ apt install libapache2-mod-auth-gssapi
增加配置 编辑Apache配置文件/etc/apache2/sites-enabled/000-default.conf,在DocumentRoot下一行加入如下内容:
1 2 3 4 5 6 <Location /> AuthType GSSAPI AuthName "GSSAPI SSO Login" GssapiCredStore keytab:/etc/apache2/http.keytab Require valid-user </Location>
其中GssapiCredStore所指向的http.keytab文件中放的是HTTP服务的密钥信息。需要在KDC Server 上为Web服务添加Principal:
1 2 3 4 5 6 kadmin.local: add_principal -randkey HTTP/tmp WARNING: no policy specified for HTTP/tmp@MYKRB.com; defaulting to no policy Principal "HTTP/tmp@MYKRB.com" created. kadmin.local: ktadd -k http.keytab HTTP/tmp Entry for principal HTTP/tmp with kvno 2, encryption type aes256-cts-hmac-sha1-96 added to keytab WRFILE:http.keytab. Entry for principal HTTP/tmp with kvno 2, encryption type aes128-cts-hmac-sha1-96 added to keytab WRFILE:http.keytab.
将上面生成的http.keytab文件复制到Web服务器并放在/etc/apache2目录下,然后重启Apache2。
1 $ systemctl restart apache2
此时在访问测试文件,会显示401 Unauthorized,GSSAPI配置已经生效:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 $ curl -i http://tmp/krb5_hello.txt HTTP/1.1 401 Unauthorized Date: Sat, 24 Oct 2020 17:03:26 GMT Server: Apache/2.4.29 (Ubuntu) WWW-Authenticate: Negotiate Content-Length: 464 Content-Type: text/html; charset=iso-8859-1 <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <html><head> <title>401 Unauthorized</title> </head><body> <h1>Unauthorized</h1> ...
客户端访问 安装客户端 安装过程中填写的与KDC Server相同,Client的/etc/krb5.conf需要与KDC Server的/etc/krb5.conf保持一致。
用户凭证 由于curl不会提示让输入Kerberos用户和密码,而是使用了当前用户的凭证缓存,先在KDC Server中添加一条测试Principal:
1 2 3 4 5 kadmin.local: add_principal test/test WARNING: no policy specified for test/test@MYKRB.com; defaulting to no policy Enter password for principal "test/test@MYKRB.com": Re-enter password for principal "test/test@MYKRB.com": Principal "test/test@MYKRB.com" created.
在客户端上生成用户凭证缓存:
1 2 3 4 5 6 7 8 9 10 $ kinit test /test Password for test/test@MYKRB.com: $ klist Ticket cache: FILE:/tmp/krb5cc_1000 Default principal: test/test@MYKRB.com Valid starting Expires Service principal 2020-10-25T02:49:53 2020-10-25T12:49:53 krbtgt/MYKRB.com@MYKRB.com renew until 2020-10-26T02:49:50
此时再通过curl进行测试:
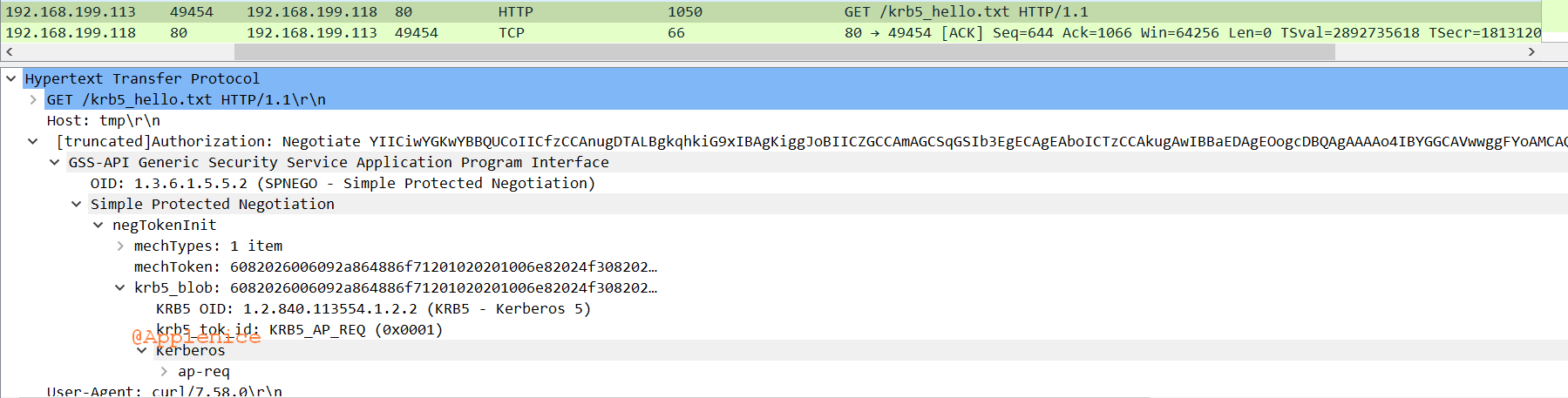
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 $ curl -i --negotiate -u: http://tmp/krb5_hello.txt HTTP/1.1 401 Unauthorized Date: Sat, 24 Oct 2020 18:50:25 GMT Server: Apache/2.4.29 (Ubuntu) WWW-Authenticate: Negotiate Content-Length: 450 Content-Type: text/html; charset=iso-8859-1 HTTP/1.1 200 OK Date: Sat, 24 Oct 2020 18:50:25 GMT Server: Apache/2.4.29 (Ubuntu) WWW-Authenticate: Negotiate oYG3MIG0oAMKAQChCwYJKoZIhvcSAQICooGfBIGcYIGZBgkqhkiG9xIBAgICAG+BiTCBhqADAgEFoQMCAQ+iejB4oAMCARKicQRvSyMiPrd4Bm4pYFVETNSQ82fBSOV0fmxr2kFGL0y1DKRDgYsq/jwr2FJrQgqc4D2K7pygd3b2ezWrS4siVPQU9P6EwQpO6Q22XCY5bjJCOST1q6RNiMou8f595Njyculryk6aEJjMgfRsHj364zLQ Last-Modified: Sat, 24 Oct 2020 15:32:55 GMT ETag: "f-5b26c6942a142" Accept-Ranges: bytes Content-Length: 15 Content-Type: text/plain Hello Kerberos
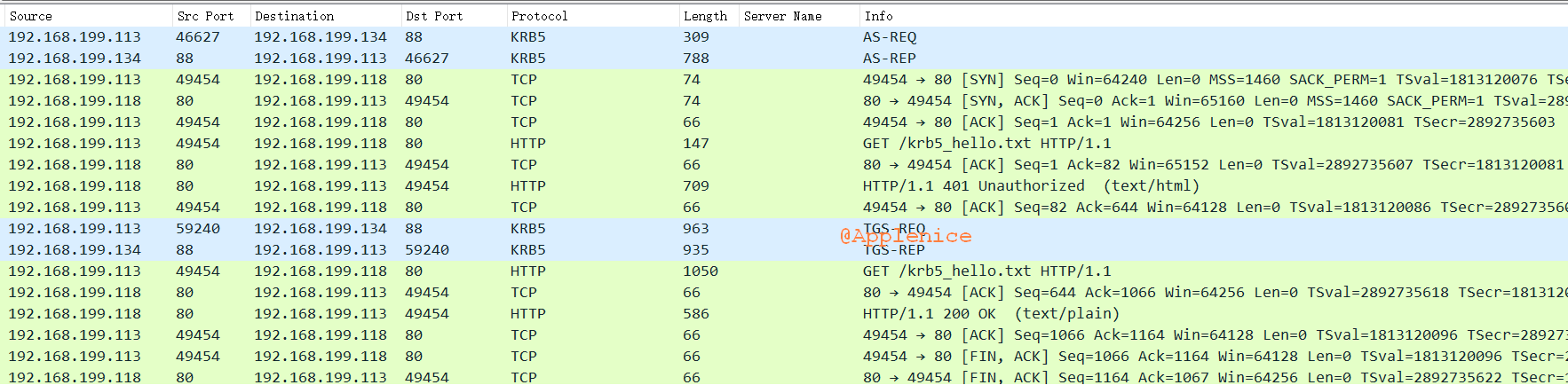
通过返回信息可以看出有两次返回,第一次仍然是401 Unauthorized,第二次返回了服务端提供的Token,能够访问krb5_hello.txt文件,说明环境搭建成功啦😆
认证过程 关于KRB5协议的交互过程,这里有篇文章讲的十分清楚:http://www.securityandit.com/network/kerberos-protocol-understanding/
参考 1、https://docs.oracle.com/cd/E19253-01/819-7056/overview-19/index.html https://027yunwei.com/shen-fen-yan-zheng/http-negotiate-spnego-kerberos-sample.html http://www.out1kiss.me/?p=538 http://www.ipfonix.com/single-sign-on.pdf https://linuxconfig.org/how-to-install-kerberos-kdc-server-and-client-on-ubuntu-18-04